This paradigm shift from a fixed workplace to a flexible one has given new freedom to employees, who are displaying enhanced productivity and achievement of goals by balancing their personal and professional life in a better way. But the rise in employee prolificacy comes with one major disadvantage. As a result, there has been a rise in handling data security, data loss, insider risk, and the challenges to conquer these risks. These risks are termed Insider Risks.
What does Insider Risk Management Solutions Include?
Insider risk involves the data exposed due to security lapse, human error, or lack of security tools, which endangers a company’s financial and operational functions. For example, an employee can accidentally create it, including data theft, data loss, data transferred to untrusted sources, etc. Code42, 2021 Data Exposure Report indicates that: Employees leaking files after Covid-19 has risen by 85%. 54% of the companies lack an Insider Response Plan.
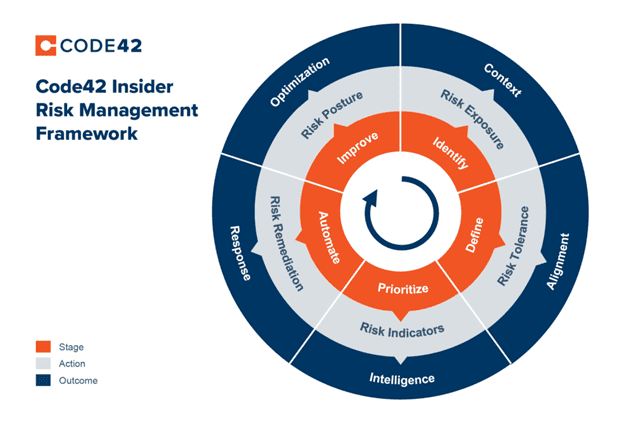
Hence, Insider Risk Management (IRM) solutions are not only restricted to employees and data, but it goes way beyond these to include the security solutions, behaviour monitoring of users, use of software and technology, and the tools involved. The foundation of IRM stands on the three main pillars. They are:
Monitoring of Files, Vectors, and Users:
Organization data is pivotal, and security lapses due to lack of monitoring, inaccurate classification, data exfiltration, or malicious employees increase insider risk. Monitoring of files and behaviour monitoring of users is one of the solutions stated by IRM.
100% Cloud-Native:
Remote working or dispersed employees are here to stay, and hence it is essential to invest in off-site security solutions. Furthermore, employees are also becoming well-versed with cloud-based tools, thus challenging the security teams to protect the data transmissions between the cloud and the end-users.
Non-disruptive to Employee Productivity or Collaboration:
You can’t ignore human error, neither can you ignore malicious employees. Employees intentionally or unintentionally expose data that can damage your finances as well as reputation. IRM solutions balance these disruptions and give the best technical solution, which helps the IT teams and security analysts prevent data exposures.
Creating an Impactful IRM Solution:
Insider Risk Management Solution is the key to securing data by complying with the concerned policies. Furthermore, without any user restrictions, this framework helps in creating more awareness about the risks involved. Depending on the risk, this Insider Risk Management Framework works on the best possible security solutions, with varied techniques that focus on the DLP (Data Loss Prevention) and include five other technical requirements. Let’s dig deep into these five Code42 IRM framework techniques that help eliminate insider risk and strengthen data security.
Identify Your Risk:
When and Where does Insider Risk Data Exposure Take Place?
When the risk is invisible, how can you control the same? The foremost step is to identify where your organization and data can be exposed to insider risk. The same can be done by monitoring and identifying all three risk factors, i.e., files, vectors, and users. However, employees sometimes click on phishing or suspicious links and share their details, which turns out to be a disaster for an organization. To prevent it, there should be proper training given to employees regarding browsing behaviour. In addition, before submitting your details, an employee should check the HTTPS or SSL certificate that should be there before a domain name. It will reduce the chances of data theft and cyber-attack. Based on this, you need to ensure an appropriate IRM framework to eradicate or lessen the risk effectively.
Define your Risk Resilience:
Define the acceptable and non-acceptable criteria in risk Now that you have clarity on where the data exposure takes place in insider risk, it’s time to define the risks your organization faces, and which ones need to be resolved on priority. Also, determine what vectors and risks are unacceptable. Few employees’ behavioural moves which pose insider risks are:
Sending zip files on personal emails Renaming file extensions File uploads via browsers Transferring files to cloud during non-office hours Generating shareable links in cloud apps Exfiltrating reports and other business data
Security teams need to figure out the severity of these actions and define the same. Later, detection of these risks and the response process to nullify them must be followed based on your specified tolerance criteria. Also read :
MacBook Pro16 New Could Feature A Surprising New Design: Apple 2022
What Is an Esim in a Phone: Usage, Updates
Google has released the second Developer Preview of Android 13
Check out the crucial time when your most pivotal data is at risk Once risk tolerance is defined, it becomes easy to decide which insider risk needs more attention than the other. Based on the same, action to prevent the same needs to be taken. Example: Exfiltration of reports or source codes, downloading suspicious files, renaming file extensions, and sharing in cloud databases are of more severity than the others. When your data securities are in place, you can visualize the insider risk indicators and prioritize them. Ensure that your IRM framework solution focuses more on such insider risk severities as compared to low-risk factors.
Automated Responses:
Automatic Responses to Insider Risk Automation is quicker than humans, and hence automatic response solutions against insider risk help decelerate data loss and other damages. But, just like varied problems don’t have a single solution, the same stands true for insider risk. Since all the insider risks may not be malevolent, the automatic response solutions made by your security teams must size up the severity and the situation before taking appropriate actions.
Improvement in Insider Risk Response:
Is your Insider Risk Response Suffice? Risks keep on changing their nature, and hence it’s essential to measure their severity and path. IRM framework security solutions should include the latest security solutions and technological processes to mitigate insider risk.
Wrapping Up:
Since organizations are becoming aware of the risks of data loss in one way (theft or leakage), they are planning to implement Insider Risk Management to detect and respond to the same. The only barrier in the above scenario is to program the IRM. Unfortunately, only 45% of the organizations have a clearly defined and documented process for managing insider risk. This makes the resolve process extremely difficult. I hope the five-step framework stated in this article helps you address your insider risks and protect your organization’s data.
Δ This paradigm shift from a fixed workplace to a flexible one has given new freedom to employees, who are displaying enhanced productivity and achievement of goals by balancing their personal and professional life in a better way. But the rise in employee prolificacy comes with one major disadvantage. As a result, there has been a rise in handling data security, data loss, insider risk, and the challenges to conquer these risks. These risks are termed Insider Risks.
What does Insider Risk Management Solutions Include?
Insider risk involves the data exposed due to security lapse, human error, or lack of security tools, which endangers a company’s financial and operational functions. For example, an employee can accidentally create it, including data theft, data loss, data transferred to untrusted sources, etc. Code42, 2021 Data Exposure Report indicates that: Employees leaking files after Covid-19 has risen by 85%. 54% of the companies lack an Insider Response Plan.
Hence, Insider Risk Management (IRM) solutions are not only restricted to employees and data, but it goes way beyond these to include the security solutions, behaviour monitoring of users, use of software and technology, and the tools involved. The foundation of IRM stands on the three main pillars. They are:
Monitoring of Files, Vectors, and Users:
Organization data is pivotal, and security lapses due to lack of monitoring, inaccurate classification, data exfiltration, or malicious employees increase insider risk. Monitoring of files and behaviour monitoring of users is one of the solutions stated by IRM.
100% Cloud-Native:
Remote working or dispersed employees are here to stay, and hence it is essential to invest in off-site security solutions. Furthermore, employees are also becoming well-versed with cloud-based tools, thus challenging the security teams to protect the data transmissions between the cloud and the end-users.
Non-disruptive to Employee Productivity or Collaboration:
You can’t ignore human error, neither can you ignore malicious employees. Employees intentionally or unintentionally expose data that can damage your finances as well as reputation. IRM solutions balance these disruptions and give the best technical solution, which helps the IT teams and security analysts prevent data exposures.
Creating an Impactful IRM Solution:
Insider Risk Management Solution is the key to securing data by complying with the concerned policies. Furthermore, without any user restrictions, this framework helps in creating more awareness about the risks involved. Depending on the risk, this Insider Risk Management Framework works on the best possible security solutions, with varied techniques that focus on the DLP (Data Loss Prevention) and include five other technical requirements. Let’s dig deep into these five Code42 IRM framework techniques that help eliminate insider risk and strengthen data security.
Identify your Risk:
When and Where does Insider Risk Data Exposure Take Place? When the risk is invisible, how can you control the same? The foremost step is to identify where your organization and data can be exposed to insider risk. The same can be done by monitoring and identifying all three risk factors, i.e., files, vectors, and users. However, employees sometimes click on phishing or suspicious links and share their details, which turns out to be a disaster for an organization. To prevent it, there should be proper training given to employees regarding browsing behaviour. In addition, before submitting your details, an employee should check the HTTPS or SSL certificate that should be there before a domain name. It will reduce the chances of data theft and cyber-attack. Based on this, you need to ensure an appropriate IRM framework to eradicate or lessen the risk effectively.
Define your Risk Resilience:
Define the acceptable and non-acceptable criteria in risk Now that you have clarity on where the data exposure takes place in insider risk, it’s time to define the risks your organization faces, and which ones need to be resolved on priority. Also, determine what vectors and risks are unacceptable. Few employees’ behavioural moves which pose insider risks are:
Sending zip files on personal emails Renaming file extensions File uploads via browsers Transferring files to cloud during non-office hours Generating shareable links in cloud apps Exfiltrating reports and other business data
Security teams need to figure out the severity of these actions and define the same. Later, detection of these risks and the response process to nullify them must be followed based on your specified tolerance criteria.
Prioritize:
Check out the crucial time when your most pivotal data is at risk Once risk tolerance is defined, it becomes easy to decide which insider risk needs more attention than the other. Based on the same, action to prevent the same needs to be taken. Example: Exfiltration of reports or source codes, downloading suspicious files, renaming file extensions, and sharing in cloud databases are of more severity than the others. When your data securities are in place, you can visualize the insider risk indicators and prioritize them. Ensure that your IRM framework solution focuses more on such insider risk severities as compared to low-risk factors.
Automated Responses:
Automatic Responses to Insider Risk Automation is quicker than humans, and hence automatic response solutions against insider risk help decelerate data loss and other damages. But, just like varied problems don’t have a single solution, the same stands true for insider risk. Since all the insider risks may not be malevolent, the automatic response solutions made by your security teams must size up the severity and the situation before taking appropriate actions.
Improvement in Insider Risk Response:
Is your Insider Risk Response Suffice? Risks keep on changing their nature, and hence it’s essential to measure their severity and path. IRM framework security solutions should include the latest security solutions and technological processes to mitigate insider risk.
Wrapping Up:
Since organizations are becoming aware of the risks of data loss in one way (theft or leakage), they are planning to implement Insider Risk Management to detect and respond to the same. The only barrier in the above scenario is to program the IRM. Unfortunately, only 45% of the organizations have a clearly defined and documented process for managing insider risk. This makes the resolve process extremely difficult. I hope the five-step framework stated in this article helps you address your insider risks and protect your organization’s data.
Δ Contact Us :- trendblog.guest@gmail.com