This way, you can prevent security leaks and keep your data secure from the inside. Along with this, modern automated tools can also show you in real-time what data is being accessed by the various users on your network. When you have this information, you will be able to prevent any leaks before they occur. The way of doing that would be to restrict the users’ permissions so that they are not able to access everything on the network. To do all of this manually is a nightmare. Why? Because there are so many users on a network and managing the permissions for each user manually can be near to impossible. Thus, what you need is an automated tool that can help you manage user access as well as notify you when there is a user accessing information that he/she is not supposed to. Thus, the Access Rights Manager by Solarwinds is a perfect match for this. It not only helps you set up user permissions but it can also monitor the network so that no ordinary user is accessing critical information. Hence, let us begin with this article.
Installing Access Rights Manager
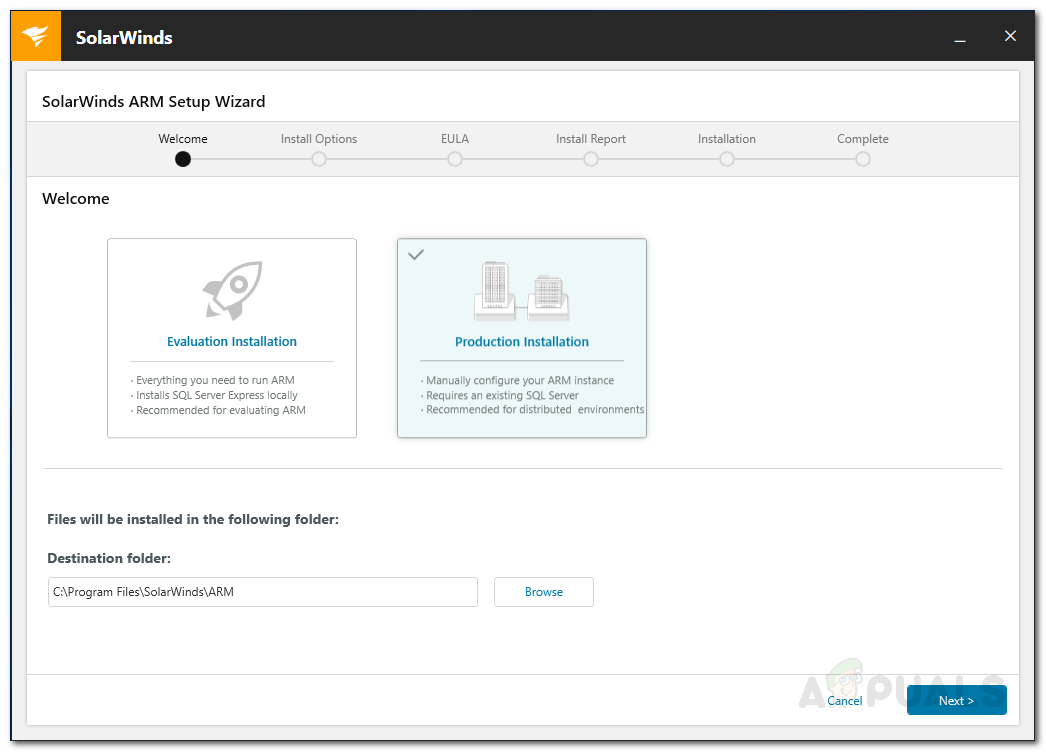
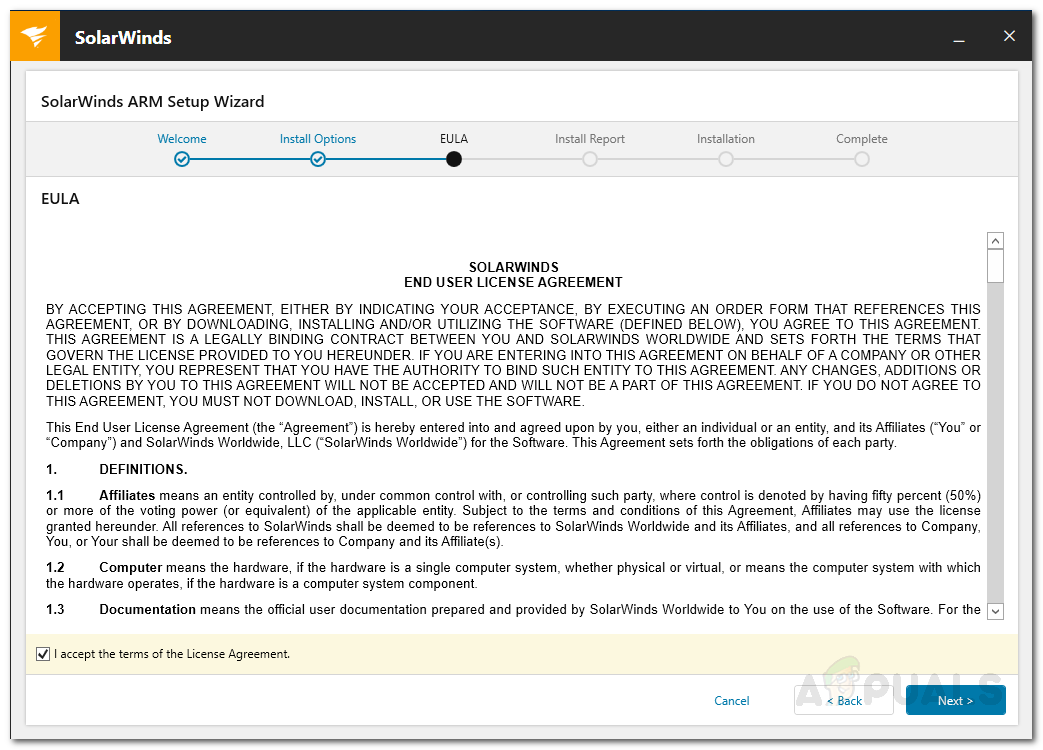
First of all, you will have to deploy the Access Rights Manager tool on your system. For this purpose, head to this link and download the tool by clicking the respective button. Once you have downloaded the tool, follow the instructions given down below to perform a successful installation:
Configuring Access Rights Manager
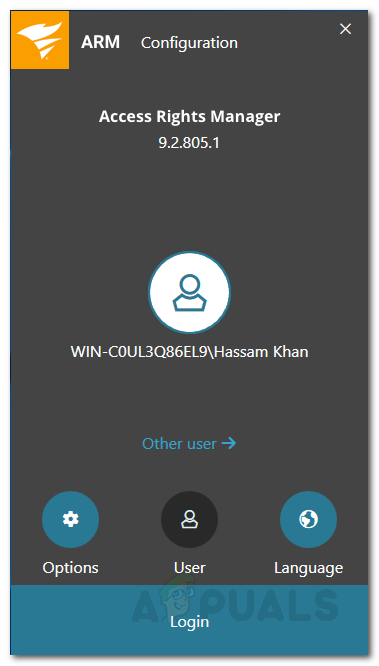
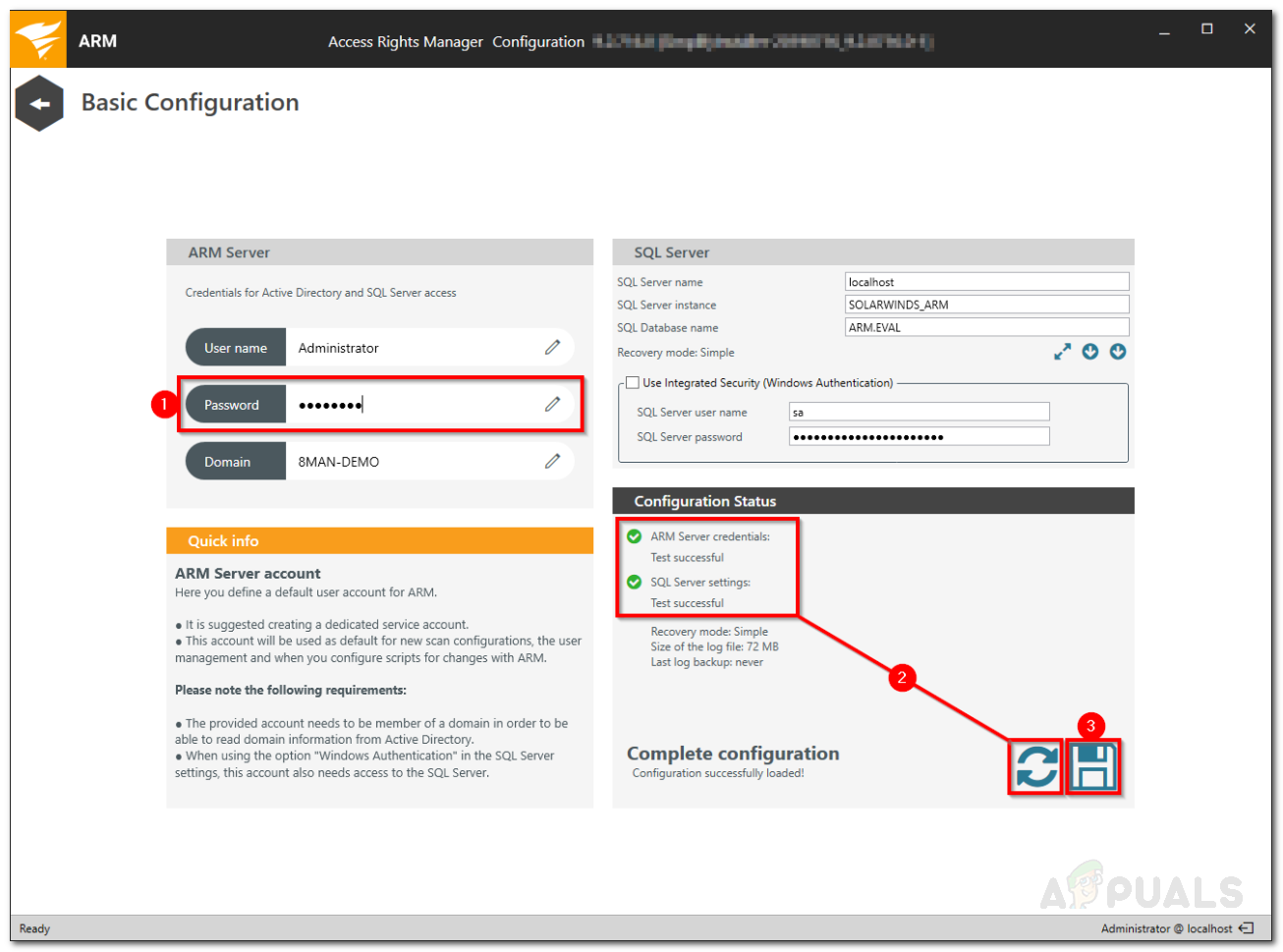
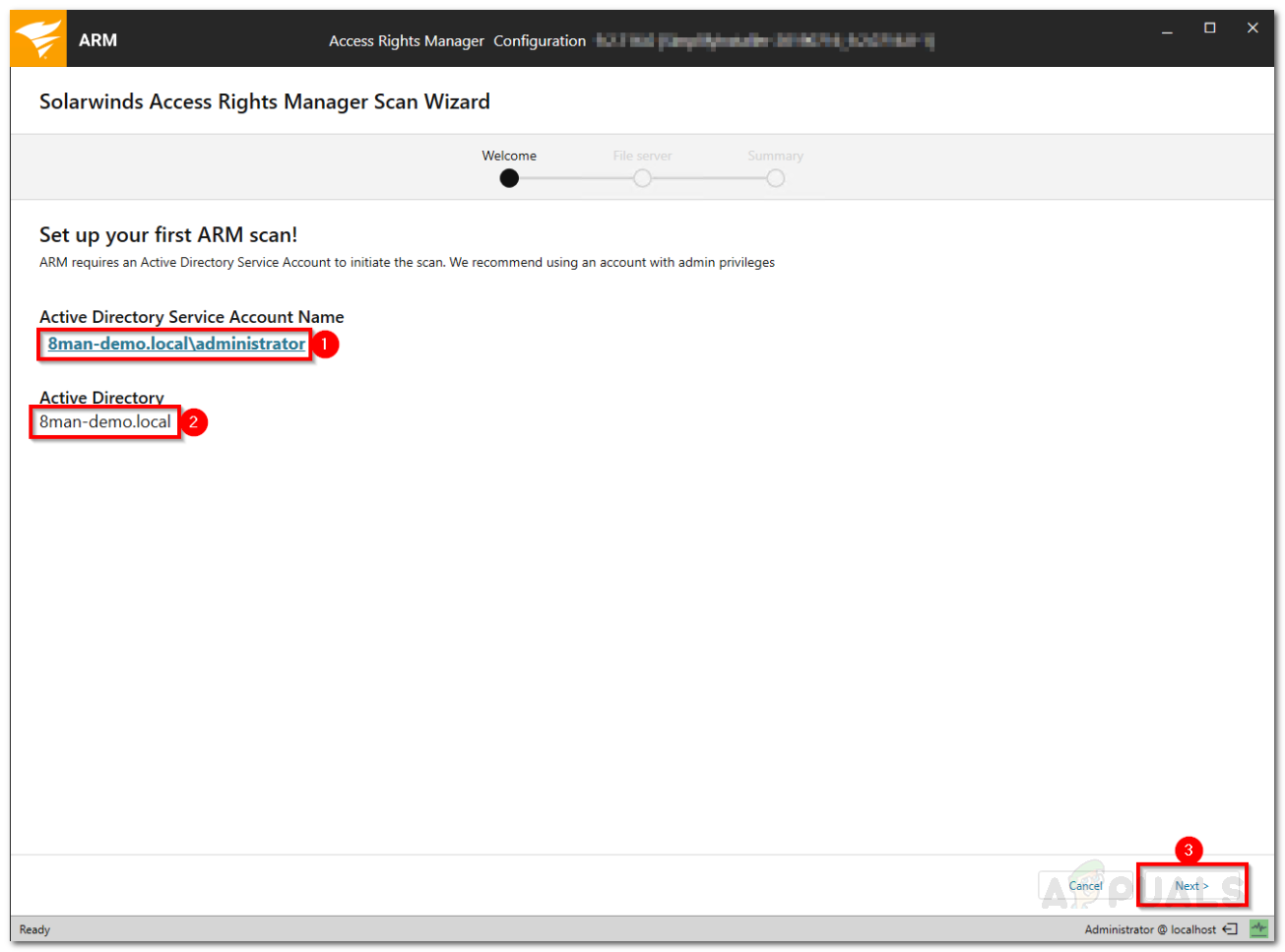
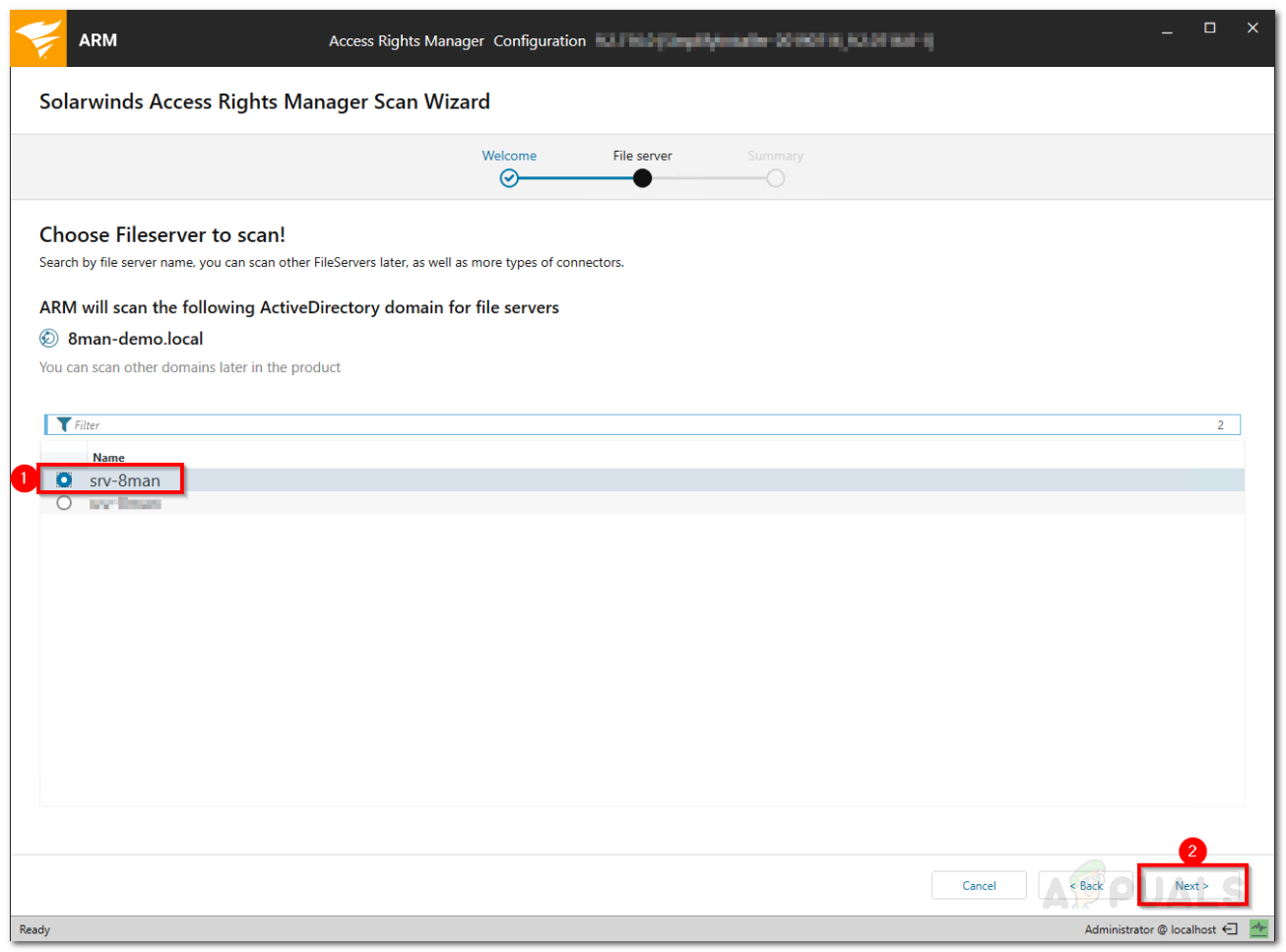
Once the tool has installed successfully on your system, you will have to perform some basic configuration before you can use Access Rights Manager. The configuration wizard is used to collect information for the first Active Directory scan and the base configuration. Once the installation wizard completes, the Configuration Wizard will load up automatically. Here’s how to configure Access Rights Manager:
Managing Access Rights
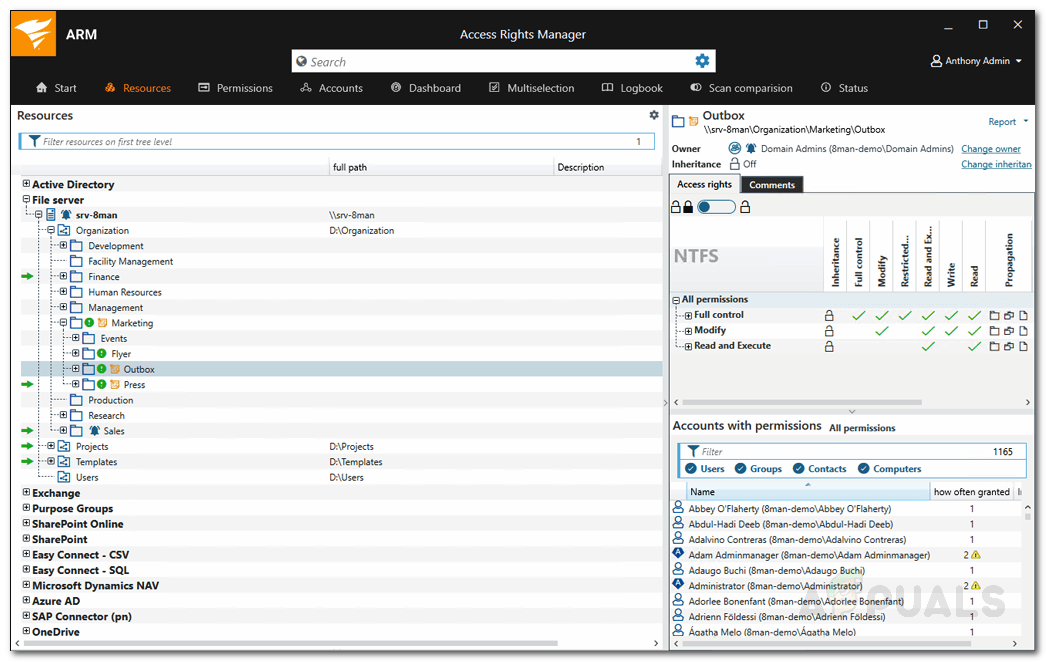
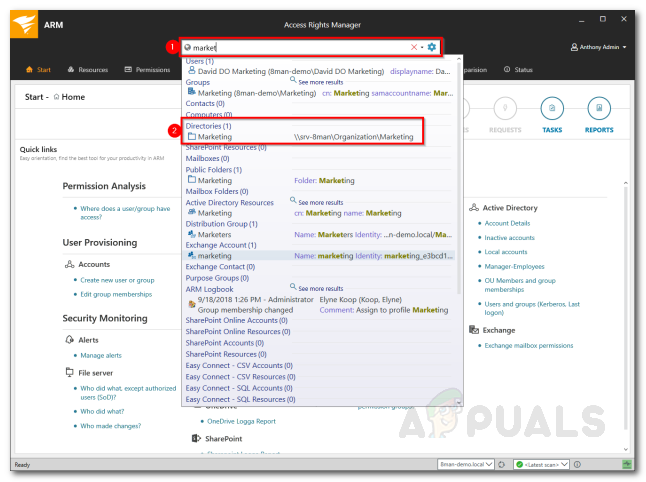
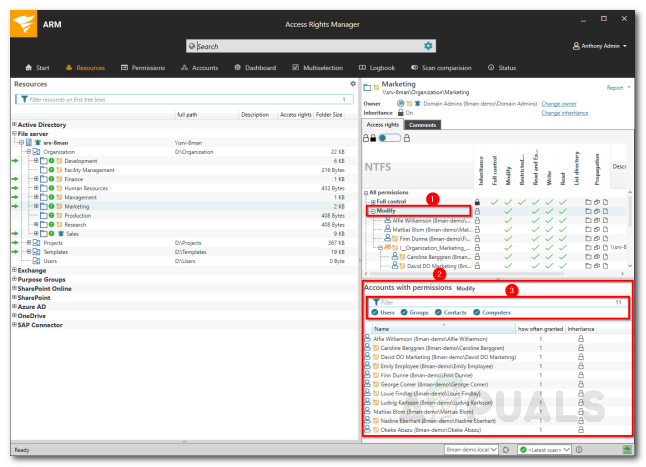
Now that you have set up everything, you can start using Access Rights Manager to view the different directories and the users that have access to it. To start, it is recommended you target the directories that have the most sensitive data and check the various users that have access to it. Here’s how to do it:
Monitoring Access to Sensitive Data
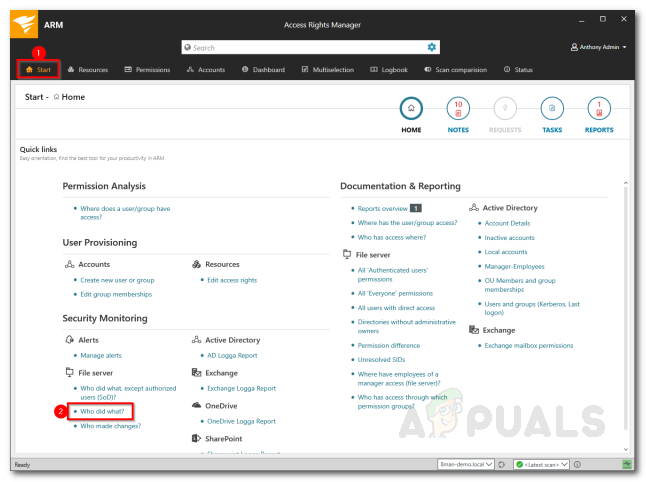
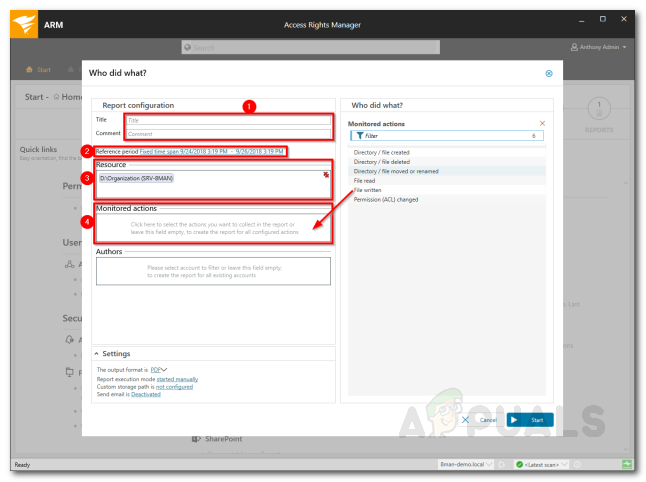
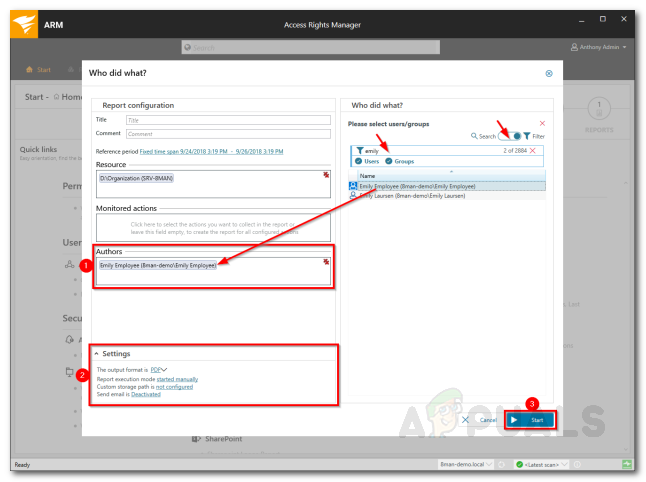
With the Access Rights Manager tool, you can monitor access to the sensitive data on your network. This will help you get notified if someone attempts to access those files. Pretty useful if you don’t want users to access the specified data. Here’s how to do it:
How to Identify Recursive and Empty Groups in Active Directory using Access…The 5 Best Access Rights Management ToolsHow to Manage User and Computer Accounts using Admin Bundle For Active…PubG Announces It Would Revoke Publications Rights from Tecent Games in India